KSA Cybersecurity Market Growth, Trends, Size, Demand, Revenue, Share and Future Competition
KSA Cybersecurity Market Size- By Security Type, By Solution Type, By Services, By End User, By Deployment Mode- Regional Outlook, Competitive Strategies and Segment Forecast to 2032
| Published: Dec-2022 | Report ID: IACT2240 | Pages: 1 - 236 | Formats*: |
| Category : Information & Communications Technology | |||
- July 2022 - Cisco introduced Talos Intel On-Demand, which tailors research to each organization's specific threat landscape, and a secure cloud that uses an open shared signals and events framework for quick data sharing between vendors to simplify the work of security analysts. For the purpose of detecting threats, its Secure Firewall 3100 series adds AI and machine learning to the mix.
- Palo Alto Networks has released Unit 42 Managed Detection and Response (Unit 42 MDR), a brand-new solution that offers continuous 24/7 threat detection, investigation, and response. Due to the use of Cortex XDR, Unit 42 MDR is designed to prioritize alerts and drastically cut down on the number of notifications that clients receive. Customers can now spot more questionable behaviour thanks to this.

| Report Metric | Details |
| Market size available for years | 2019-2032 |
| Base year considered | 2021 |
| Forecast period | 2022-2032 |
| Segments covered | By Security Type, By Solution Type, By Services, By End User, By Deployment Mode |
| Regions covered | Northern, Western, Eastern, Central, Southern |
| Companies Covered | Al Moammar Information Systems Co., Broadcom Inc., Check Point Software Technologies Ltd., Cipher, Cisco Systems Inc., Dell Technologies, FireEye Inc., Fortinet Inc., Hewlett Packard Enterprise, IBM Corporation, Kaspersky Lab, Lockheed Martin Corporation, NEC Saudi Arabia Ltd., Norton LifeLock Inc., Palo Alto Networks Inc., SAT Microsystems, Sirar by STC, Tenable Inc., Trellix, Trend Micro Incorporated |
- Government and Regulatory Bodies
- Enterprises and Businesses
- Critical Infrastructure Operators
- Small and Medium-sized Enterprises
- Cybersecurity Vendors and Service Providers
- Cybersecurity Professionals and Experts
| By Security Type: |
|
| By Solution Type: |
|
| By Services: |
|
| By End User: |
|
| By Deployment Mode: |
|
- KSA Cybersecurity Market Size (FY’2022-FY’2032)
- Overview of KSA Cybersecurity Market
- Segmentation of KSA Cybersecurity Market By Security Type (Application Security, Cloud Security, Content Security, Endpoint Security, Network Security, Others (operational security, e-mail security, etc.))
- Segmentation of KSA Cybersecurity Market By Solution Type (Antivirus & Antimalware, Data Loss Prevention, Encryption & Decryption, Firewall, Identity & Access Management, Infrastructure Security, Intrusion Detection/Prevention System, Risk & Compliance Management, Unified Threat Management, Others (Denial-of-service attack, malware, man-in-the-middle-attack, drive-by-downloads, etc.))
- Segmentation of KSA Cybersecurity Market By Services (Consulting, Design and Integration, Risk and Threat Assessment, Managed Security Service, Training and Education)
- Segmentation of KSA Cybersecurity Market By End User (Aerospace, Defense and Intelligence, Banking and Financial Service Institutes, Corporates/Private Organizations, Education Technology, Government and Public Utilities, Healthcare, Manufacturing, Retail, Telecom and IT, Others)
- Segmentation of KSA Cybersecurity Market By Deployment Mode (Cloud, On-premises)
- Statistical Snap of KSA Cybersecurity Market
- Expansion Analysis of KSA Cybersecurity Market
- Problems and Obstacles in KSA Cybersecurity Market
- Competitive Landscape in the KSA Cybersecurity Market
- Impact of COVID-19 and Demonetization on KSA Cybersecurity Market
- Details on Current Investment in KSA Cybersecurity Market
- Competitive Analysis of KSA Cybersecurity Market
- Prominent Players in the KSA Cybersecurity Market
- SWOT Analysis of KSA Cybersecurity Market
- KSA Cybersecurity Market Future Outlook and Projections (FY’2022-FY’2032)
- Recommendations from Analyst
1.1. Scope of the report1.2. Market segment analysis
2.1 Research data source
2.1.1 Secondary data2.1.2 Primary data2.1.3 SPER’s internal database2.1.4 Premium insight from KOL’s
2.2 Market size estimation
2.2.1 Top-down and Bottom-up approach
2.3 Data triangulation
4.1. Driver, Restraint, Opportunity and Challenges analysis
4.1.1 Drivers4.1.2 Restraints4.1.3 Opportunities4.1.4 Challenges
4.2. COVID-19 Impacts of the KSA Cybersecurity Market
5.1. SWOT analysis
5.1.1 Strengths5.1.2 Weaknesses5.1.3 Opportunities5.1.4 Threats
5.2. PESTEL analysis
5.2.1 Political landscape5.2.2 Economic landscape5.2.3 Social landscape5.2.4 Technological landscape5.2.5 Environmental landscape5.2.6 Legal landscape
5.3. PORTER’S five forces analysis
5.3.1 Bargaining power of suppliers5.3.2 Bargaining power of Buyers5.3.3 Threat of Substitute5.3.4 Threat of new entrant5.3.5 Competitive rivalry
5.4.Heat map analysis
6.1. KSA Cybersecurity Base Distribution, Sales Area, Product Type6.2. Mergers & Acquisitions, Partnerships, Product Launch, and Collaboration in KSA Cybersecurity Market
7.1. Application Security7.2. Cloud Security7.3. Content Security7.4. Endpoint Security7.5. Network Security7.6. Others (operational security, e-mail security, etc.)
8.1. Antivirus & Antimalware8.2. Data Loss Prevention8.3. Encryption & Decryption8.4. Firewall8.5. Identity & Access Management8.6. Infrastructure Security8.7. Intrusion Detection/Prevention System8.8. Risk & Compliance Management8.9. Unified Threat Management8.10. Others (Denial-of-service attack, malware, man-in-the-middle-attack, drive-by-downloads, etc.)
9.1. Consulting, Design and Integration9.2. Risk and Threat Assessment9.3. Managed Security Service9.4. Training and Education
10.1. Aerospace, Defense and Intelligence10.2. Banking and Financial Service Institutes10.3. Corporates/Private Organizations10.4. Education Technology10.5. Government and Public Utilities10.6. Healthcare10.7. Manufacturing10.8. Retail10.9. Telecom and IT10.10. Others
11.1. Cloud11.2. On-premises
12.1. KSA Cybersecurity Size and Market Share by Region (2019-2025)12.2. KSA Cybersecurity Size and Market Share by Region (2026-2032)
12.3. Northern Saudi Arabia
12.4. Western Saudi Arabia
12.5. Eastern Saudi Arabia
12.6. Central Saudi Arabia12.7. Southern Saudi Arabia
13.1. Al Moammar Information Systems Co.
13.1.1. Company details13.1.2. Financial outlook13.1.3. Product summary13.1.4. Recent developments
13.2. Broadcom Inc.
13.2.1. Company details13.2.2. Financial outlook13.2.3. Product summary13.2.4. Recent developments
13.3. Check Point Software Technologies Ltd.
13.3.1. Company details13.3.2. Financial outlook13.3.3. Product summary13.3.4. Recent developments
13.4. Cipher
13.4.1. Company details13.4.2. Financial outlook13.4.3. Product summary13.4.4. Recent developments
13.5. Cisco Systems Inc.
13.5.1. Company details13.5.2. Financial outlook13.5.3. Product summary13.5.4. Recent developments
13.6. Dell Technologies
13.6.1. Company details13.6.2. Financial outlook13.6.3. Product summary13.6.4. Recent developments
13.7. FireEye Inc.
13.7.1. Company details13.7.2. Financial outlook13.7.3. Product summary13.7.4. Recent developments
13.8. Fortinet Inc.
13.8.1. Company details13.8.2. Financial outlook13.8.3. Product summary13.8.4. Recent developments
13.9. Hewlett Packard Enterprise
13.9.1. Company details13.9.2. Financial outlook13.9.3. Product summary13.9.4. Recent developments
13.10. IBM Corporation
13.10.1. Company details13.10.2. Financial outlook13.10.3. Product summary13.10.4. Recent developments
13.11. Kaspersky Lab
13.11.1. Company details13.11.2. Financial outlook13.11.3. Product summary13.11.4. Recent developments
13.12. Lockheed Martin Corporation
13.12.1. Company details13.12.2. Financial outlook13.12.3. Product summary13.12.4. Recent developments
13.13. NEC Saudi Arabia Ltd.
13.13.1. Company details13.13.2. Financial outlook13.13.3. Product summary13.13.4. Recent developments
13.14. Norton LifeLock Inc.
13.14.1. Company details13.14.2. Financial outlook13.14.3. Product summary13.14.4. Recent developments
13.15. Palo Alto Networks Inc.
13.15.1. Company details13.15.2. Financial outlook13.15.3. Product summary13.15.4. Recent developments
13.16. SAT Microsystems
13.16.1. Company details13.16.2. Financial outlook13.16.3. Product summary13.16.4. Recent developments
13.17. Sirar by STC
13.17.1. Company details13.17.2. Financial outlook13.17.3. Product summary13.17.4. Recent developments
13.18. Tenable Inc.
13.18.1. Company details13.18.2. Financial outlook13.18.3. Product summary13.18.4. Recent developments
13.19. Trellix
13.19.1. Company details13.19.2. Financial outlook13.19.3. Product summary13.19.4. Recent developments
13.20. Trend Micro Incorporated
13.20.1. Company details13.20.2. Financial outlook13.20.3. Product summary13.20.4. Recent developments
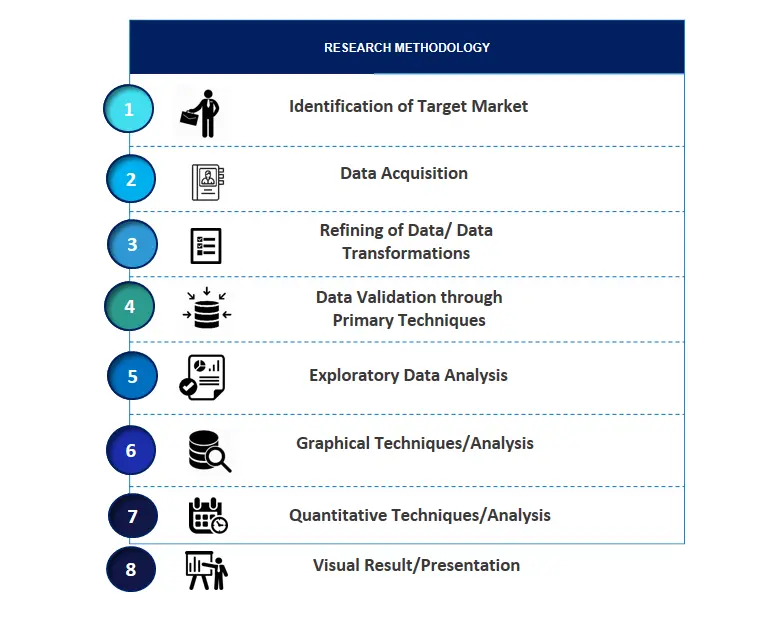
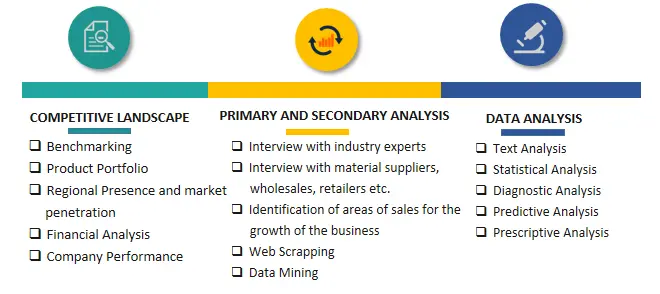
SPER Market Research’s methodology uses great emphasis on primary research to ensure that the market intelligence insights are up to date, reliable and accurate. Primary interviews are done with players involved in each phase of a supply chain to analyze the market forecasting. The secondary research method is used to help you fully understand how the future markets and the spending patterns look likes.
The report is based on in-depth qualitative and quantitative analysis of the Product Market. The quantitative analysis involves the application of various projection and sampling techniques. The qualitative analysis involves primary interviews, surveys, and vendor briefings. The data gathered as a result of these processes are validated through experts opinion. Our research methodology entails an ideal mixture of primary and secondary initiatives.
Frequently Asked Questions About This Report
PLACE AN ORDER
Year End Discount
Sample Report
Pre-Purchase Inquiry
NEED CUSTOMIZATION?
Request CustomizationCALL OR EMAIL US
100% Secure Payment






Related Reports
Our Global Clients
Our data-driven insights have influenced the strategy of 200+ reputed companies across the globe.